
How To Defend Against Vishing Attacks
Vishing attacks are just one of many types of cyberattacks that threaten everyone who owns a piece of technology. Vishing specifically focuses on the use of phones and targets innocent people through calls that are deceivingly trustworthy and can lead to identity fraud or other crimes.
Though vishing attacks can happen to anybody, senior citizens are often at higher risk for being victims because they have less experience with technology and tend to have a more trusting nature. However, there are steps you can take through education and technology to defend yourself and others against vishing attacks.
Vishing attacks are so common and deceiving that the criminals often end up getting what they want. Following a vishing attack, there are steps you can take to recover quickly and help prevent others from being taken advantage of in the same way.
What Is a Vishing Attack?
A vishing attack is a cyberattack in which a criminal calls a victim and pretends to be someone they are not to gain money, information, access to your computer or accounts, or all three. The caller could be a real person or automation, but they often create a sense of urgency using social engineering tactics that make you trust them and feel like you must take action immediately at the risk of severe consequence.
Social engineering is a broad term used to describe malicious activities done through human interaction. Whatever the situation, it uses psychological manipulation to trick someone into thinking and doing something they normally would not.
Social engineering has a life cycle:
- Investigation: The criminal begins preparing the ground for the attack and learning everything they can about the people they are trying to steal from.
- Hook: This is when the caller engages you and begins to tell you a story that you want to believe in some form or another. They want to have complete control of the interaction from the beginning. Being unaware and unprepared for the situation makes people vulnerable for this part of the cycle to take hold.
- Play: Once they’ve laid the groundwork, a visher will expand their tactics and begin getting into the technical details of their ruse. This is the stage when they will actually ask for your data.
- Exit: Vishers will finish their facade by ending the conversation without arousing any suspicion. They will cover their tracks and assure that if you weren’t suspicious already, you definitely won’t be at this point.
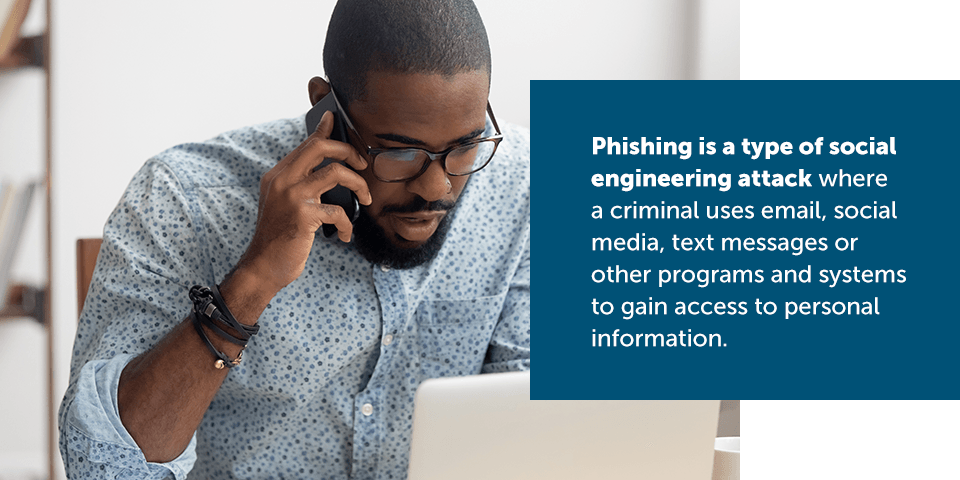
Vishing is short for “voice phishing.“ Phishing is a type of social engineering attack where a criminal uses email, social media, text messages or other programs and systems to gain access to personal information.
Vishing attacks can happen to anyone. You may have received a vishing call already today. Some are at much higher risk for succumbing to the attempt, especially if their job requires them to provide information to callers often. Vishers also tend to prey more heavily on the emotionally vulnerable.
How Are Vishing Attacks Performed?
Vishing always occurs over the phone, and the goal is always for someone to act and often give up some sort of information. Vishing attacks use a lot of psychology. Attackers target average people by posing as a person of authority.
Sometimes, vishers approach the situation acting like they are trying to help, while other times, it is a much more forceful conversation. Regardless, they want the person on the end to feel they are doing the right thing or have no other choice.
How Do You Identify a Vishing Attack?
You can identify vishing scams through the caller’s use of scare tactics. They may attempt to create a sense of urgency, like telling you you’re behind on bill payments, to encourage you to act without questioning them.
Typically, though, vishing attacks are a process. They often start with a “validation call,” which is the visher’s way of validating how real your number is. When you answer, they know to call back because they know a real person owns the number. Letting unknown numbers go to voicemail can help limit the number of vishing attacks you get.
Knowing what type of information vishers will ask for will also help you identify when a vishing attack is happening. Often, vishers will be seeking your social security number, bank or credit card information or passwords to various accounts. Vishers might even make up an issue with your computer, which is also a red flag. With the ability to control your computer, vishers can access personal data, like logins or credit card details.
You should also be aware that vishing attacks happen more often at certain times of the year. For example, vishers often impersonate the Internal Revenue Service (IRS) or tax prep firms during tax season. You may get more calls from people pretending to be political organizations or campaigns seeking financial support in an election season. In the wake of a natural disaster or tragedy, vishers may come out stronger and under the guise of charities looking for financial support to provide relief to the victims.
Over-the-phone scams outside of those times can also include calls about a vehicle’s warranty or about loans.
Types of Vishing Attacks
Criminals performing vishing attacks can take on a number of personas. Here are some common examples of vishing attacks:
- Government: Attackers will pretend to be from the government and say they are calling due to your unpaid taxes. They often threaten quick and severe consequences like jail time if you do not act quickly. They will ask for your credit card information over the phone to complete the transaction. However, the government will often only send official tax notifications by regular mail.
- Tech companies: Other times, callers will pretend to be from a tech company such as Amazon, Apple or Microsoft and tell you your device has been infected. Their goal is either for you to try to buy new software or give them remote access to your computer.
- Bank or credit card: Another common tactic for attackers is to pretend to be your bank account or credit card company. They often leave a voicemail that gives you a number to call back. When you call the number, they ask you to confirm your identity using questions that will allow them to hack into your accounts and commit identity fraud and theft.

How Do You Defend Against Vishing Attacks?
Apart from knowing the signs of a vishing attack, there are other things you can do to defend against attacks when they happen:
1. BE WARY OF CALLER ID
Though caller ID is a great tool, vishers know how to make the number seem trustworthy when it is not. Even if a caller has a trustworthy or recognizable area code, it is safer to send it to voicemail if you are unsure.
2. DON’T GIVE THEM COMPUTER CONTROL
Never give a caller control over your computer, no matter their reasoning. If you’re having issues with a piece of technology, take it to a reputable repair company or contact one for yourself. If you haven’t been having technology issues, you have all the more reason to be suspicious of calls claiming you do.
Similarly, avoid navigating to a website the caller tells you to go to or offering your email address to suspicious callers.
3. HANG UP
The best thing you can do to protect yourself from a scam is to simply hang up as soon as suspicions arise. If the call doesn’t seem suspicious at first, consider who the caller says they are and what they’re asking you.
Your bank or credit card company will never ask for your account information unless you placed the call to them and they are serving you. If you receive a call that asks for this information, it is a scam. If you’re unsure if a company is actually returning your call, it’s best to err on the side of caution and hang up.
If you are concerned that it could’ve been an organization you trust, hang up and then call that organization yourself so you can know for sure.
4. LET IT GO TO VOICEMAIL
If you do not recognize a number, simply let it go to voicemail. This gives you the ability to make the judgment call without someone asking you questions and pressuring you. If it is an organization you trust, you can simply return the call.
5. ASK FOR PROOF
There is no reason you cannot ask the person on the other end of the line to prove their identity. This will settle your mind if you are unsure if you are experiencing a vishing attack or not. If the organization is legitimate, they will have no problem proving their identity.
6. PROTECT YOUR INFORMATION
A good rule of thumb is simply to never share sensitive or personal information over the phone, no matter how confident or official the caller sounds. Never offer your social security number, credit card or bank information to someone who’s called you. Avoid answering personal questions that could be security queries for accounts, as well, like grandparents’ first names or streets you’ve lived on.
How Do You Recover From a Vishing Attack?
If you have been the victim of a vishing attack, there are steps you can take to minimize the damage as much as possible:
- Report to the Federal Trade Commission (FTC): The FTC asks people report vishing calls to them so they can eliminate them when possible. They will ask you for information like the caller ID that appeared, what time they called and what information they asked you for.
- Contact service providers: Contact the people who store the information you believe was compromised, such as your bank, credit card company or phone provider.
- Review multifactor devices: Some accounts let you authorize or remember certain devices, like a phone you log into a social media account on. If you use multifactor authentication (MFA), check the authorized devices and make sure there aren’t any that shouldn’t be there, such as a new phone or browser in a different location.
- Change your passwords: You should go through your accounts and change your passwords to lock out whoever got access to your information.

How to Protect Senior Citizens From Vishing Attacks
Senior citizens can be more vulnerable to vishing attacks. According to the FBI, victims of fraud over 60 years old accounted for $835 million in losses in 2019.
Some senior citizens might have trouble adapting to technology quickly as it has advanced rapidly in their lifetime. Their passwords may not be very strong or protected by multifactor authentication. When alerts and warnings come up, they may not be as likely to pay attention to them. Senior citizens might also be more trustworthy and willing to talk to whoever calls.
The best thing you can do to protect senior living facility residents from vishing attacks is share with them what you know about cybersecurity. Patiently teach them about it so they have the same defenses you do. You can also take it upon yourself to implement safety measures onto their various accounts if you can and they allow it. From there, take these steps:
- Enable multifactor authentication: Teaching senior citizens how to use multifactor authentication is a worthwhile investment of your time. Multifactor authentication could include facial scans or fingerprint reads, or it might involve getting a code from a phone call, email or text. Once they get used to the extra step when logging in, it won’t be a hassle and will keep their accounts more secure.
- Check passwords: Ask senior citizens what their passwords are like. Check that they are secure passwords and explain to them what could make them stronger. Also, find a secure way to help them remember their new passwords if they change them. A passphrase can offer greater protection and be easier to remember since it involves multiple words that make a sentence.
- Offer resources: Encourage them to learn more about technology and how to be safe with it. Show them resources they can use, like from government websites, to learn more in their own time.
- Teach awareness: The best thing senior citizens can do to protect against any sort of cyberattack is to simply be aware that it can happen. Since they did not grow up with technology, it can be difficult to understand the risk. Making them aware of the different types of attacks and how common each one is can help protect them from falling prey to one.

Contact Prelude Services for Coverage From Vishing Attacks
Prelude Services seeks to provide innovative and secure IT solutions to the healthcare industry in the senior citizen setting. We strive to improve healthcare organizations’ data security and quality of service. The senior living and care market has seen a demand for IT services that we seek to fill. We want those organizations to focus on providing the best care possible to their patients while we handle their technological needs.
At Prelude Services, we have the technology to help you protect against vishing attacks. Our team is equipped with experts ready to help you find the best prevention plan for your needs and implement it into your workflow.
Throughout the process, we have a 24/7 service desk to answer your questions as soon as possible so you don’t have to wait should you encounter a problem and need a fast resolution.
Contact Prelude Services today to get your organization set up to be best protected from cyberattacks.
CONTACT PRELUDE SERVICES FOR 24/7 IT SUPPORT
Technology has become a crucial part of the modern business experience. Without functional computers and mobile phones, many business practices would grind to a halt. Unfortunately, breakdowns and malfunctions are an inevitable part of any machine, meaning businesses do grind to a halt until the issues are fixed. In order to keep your business running, it's crucial to have access to IT support when you experience technical difficulties.
If you're a healthcare company, long-term care provider, or small business in need of IT support at all hours, consider Prelude Services. We're a SSAE SOC
Compliant business dedicated to improving your security and functionality. We offer specific IT services for senior living care, nursing homes, retirement home services and assisted living, including 24/7 IT support. If you want to know how Prelude can help you, contact us today!
